Requesting a Certificate for an Internal CA is an article that explains how to request a Certificate for an Internal CA using a Certificate Signing Request (CSR) file.
We have an article that explains how to create an Internal CA with AD CS on Windows Server. Click here to access this article.
Also, we have an article that explains how to create the Certificate Signing Request (CSR) with OpenSSL. Click here to access this article.
At this point, we have the CSR file. This file content is shown in the picture below:
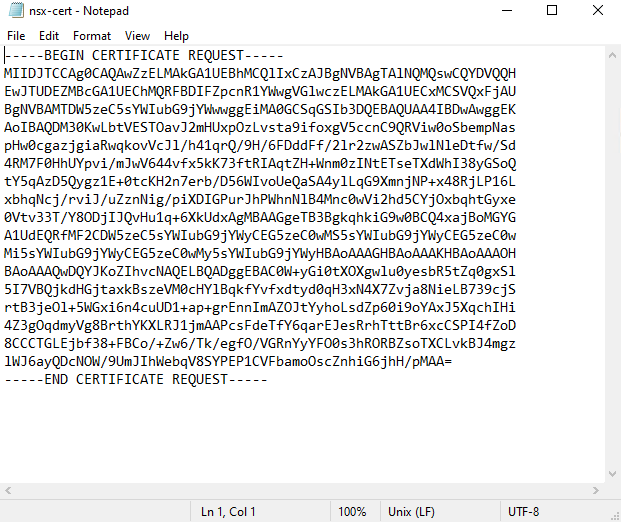
Accessing the CA Web Site and Requesting the Certificate
Our CA is based on the AD CS service on Windows Server.
So, we need to open the CA Web Page and click on “Request a certificate”:
Later, click on “advanced certificate request”:
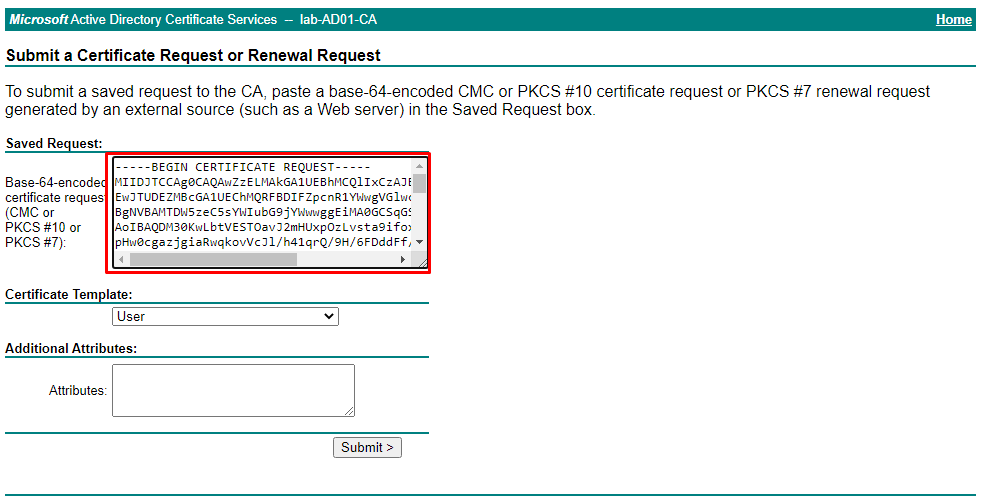
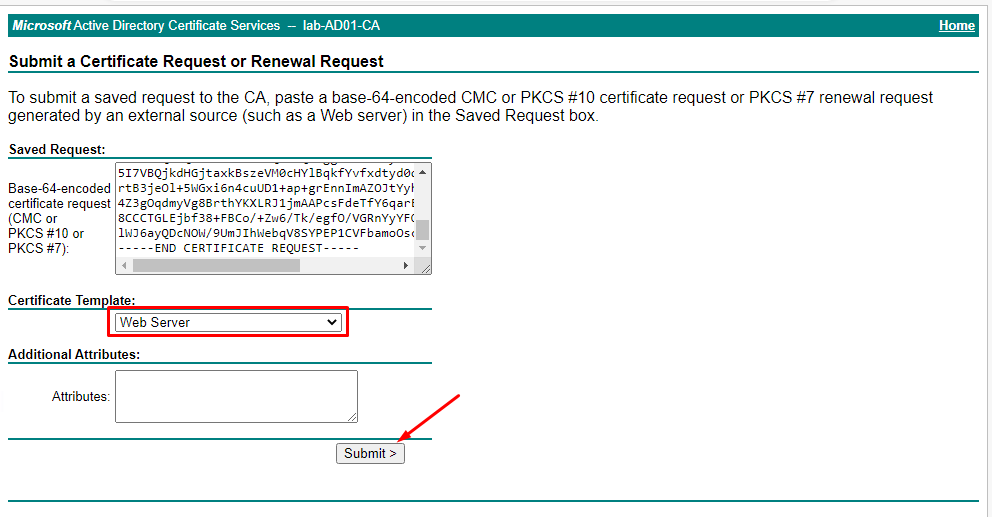
We need to copy the CSR file content and past it inside the box “Base-64-encoded certificate request”, as shown in the below picture:
Note: The CSR file content has a delimitation starting with
—–BEGIN CERTIFICATE REQUEST—–
and ending
—–END CERTIFICATE REQUEST—–
Be careful and copy/paste all file content correctly!
After that, change the Certificate Template to “Web Server” (in this case, we will use this certificate in our HTTPS website, for example).
So, click on “Submit” to send the Certificate Request to the CA:
After a few seconds, the final certificate is ready to download.
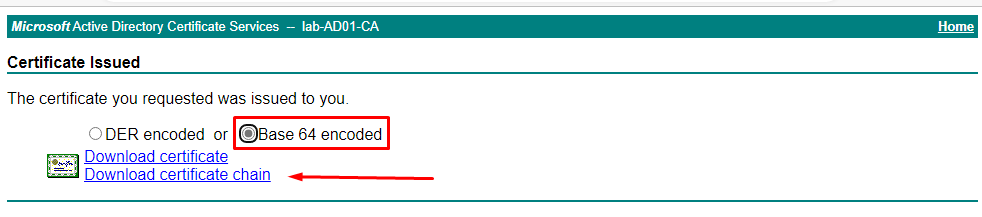
You can choose the certificate encoded and then click on Download.
Note: The are two types of certificate encoding available:
DER encoded
Base 64 encoded
For most types of usage, the Base 64 encoded is sufficient and can be used. Select this type and then click on “Download certificate chain”:
Note: By default, when you click on “Download certificate chain”, a .p7b file will be downloaded:
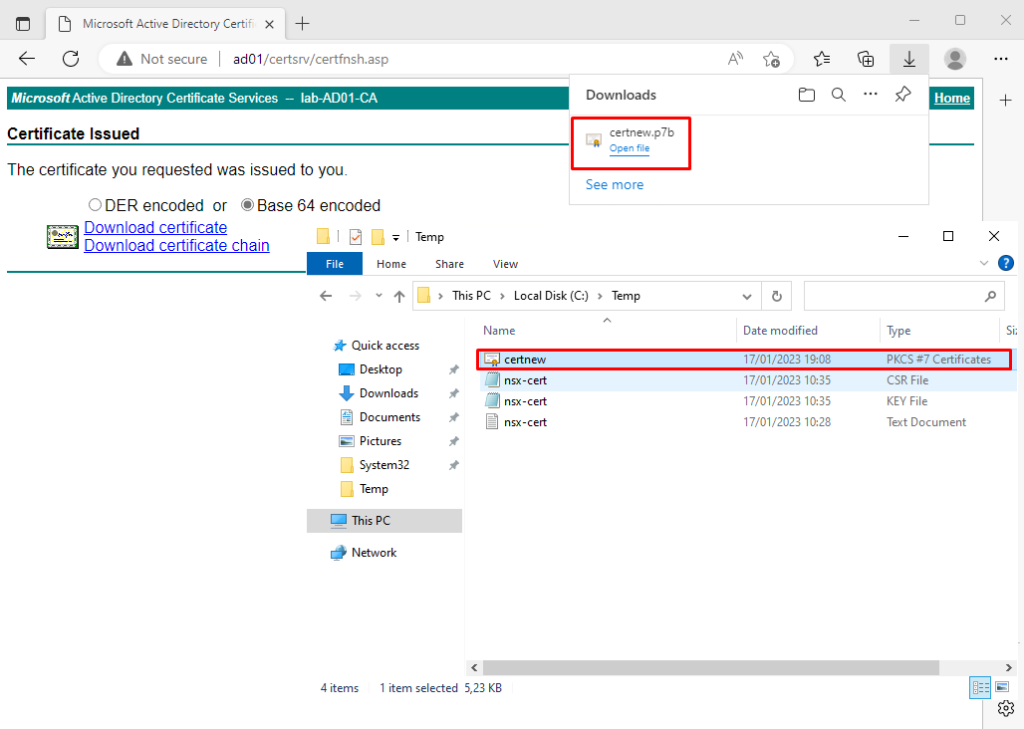
You can double-click on this file. We will see both certificates:
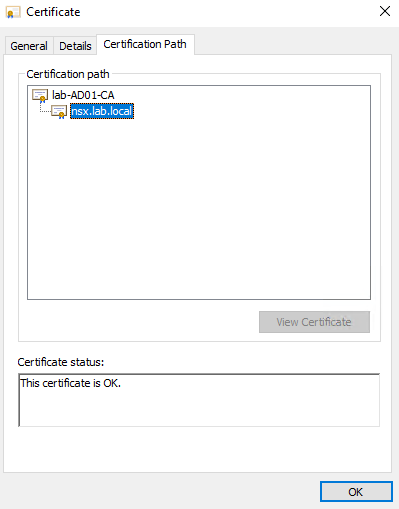
lab-AD01-CA = This is the CA certificate. We can consider it as the “root” certificate and this certificate needs to be installed too
nsx.lab.local = This is the certificate assigned by the CA and generated with the CSR file
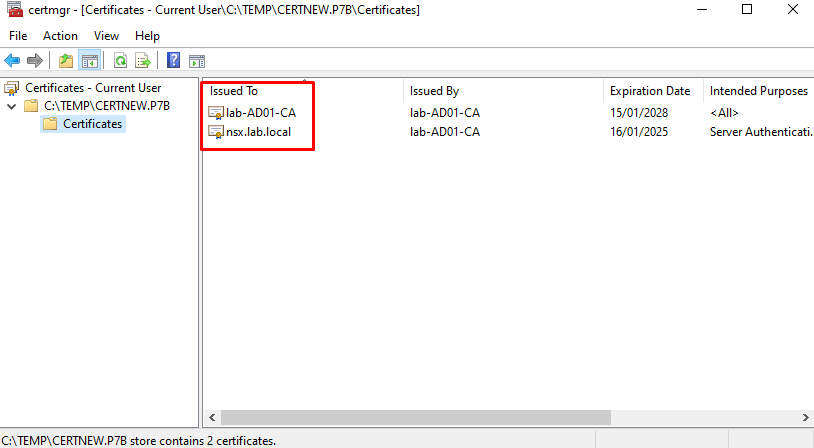
You can double-click on the certificate to get more details:
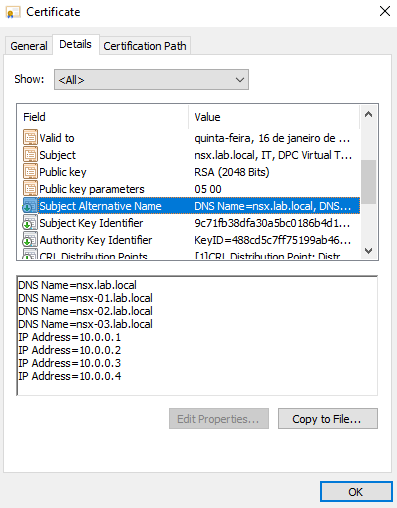
At this point, you can install this certificate in your HTTPS website, for example 🙂